It is good practice to verify the DERO binaries & match their checksum.
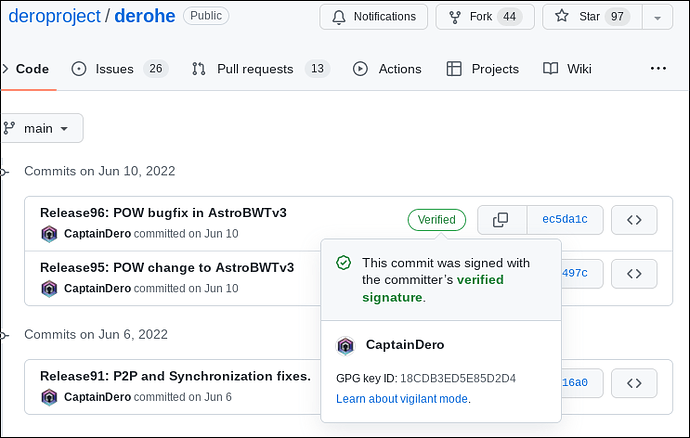
DERO GPG signed key ID: 18CDB3ED5E85D2D4.
1] Download Captain’s GPG public key which is used to sign the binaries checksum file & code.
wget https://raw.githubusercontent.com/deroproject/documentation/master/captainKEY2.asc
2] Import Captain’s GPG public & verify signature of imported key.
gpg --import captainKEY2.asc
gpg: key 0x18CDB3ED5E85D2D4: public key "Captain DeroProject (lotr824) <captain@dero.io>" imported
gpg: Total number processed: 1
gpg: imported: 1
3] Download GPG signed checksum file included with every release, mostly latest release.
wget https://github.com/deroproject/derohe/releases/latest/download/checksum.txt.asc
4] Verify the checksum file for any tamper or changes.
gpg --verify checksum.txt.asc
gpg: Signature made Fri 10 Jun 2022 09:09:43 AM UTC
gpg: using RSA key DED1FEF44297A15CAD9AE28318CDB3ED5E85D2D4
gpg: Good signature from "Captain DeroProject (lotr824) <captain@dero.io>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: DED1 FEF4 4297 A15C AD9A E283 18CD B3ED 5E85 D2D4
gpg: WARNING: not a detached signature; file 'checksum.txt' was NOT verified!
Above checksum file is verified & good.
Now verified the sha512 of the binary you have downloaded.
sha512sum dero_linux_amd64.tar.gz 288ec9af585d3cfb5c55b0a13eeed14f66a5551f6ed893cb4a214dc88f5336143a44367034b0c3c7bf85240f5b8ef450dcb376e1cb857546776261f6aa30f101 dero_linux_amd64.tar.gz
Above hash matches with hash in checksum.txt.asc file. So all good & verified.
Also code commits are signed on DERO Project Github repo, Please check for verified signature. Avoid using source code if commits are not green & GPG signed by above key.